Today, we will discuss how does a hash help secure blockchain technology.
Blockchain technology has completely transformed various industries by introducing a decentralized and transparent ledger system. It’s like a digital ledger that everyone can access and verify, removing the need for intermediaries.
However, ensuring the security of transactions is crucial for blockchain to function effectively. This is where hash functions come into play.
In this blog post, we’ll explore why security is so crucial in blockchain and how these little hashes significantly keep our digital transactions safe and reliable.
So, let’s dive in and uncover the secrets behind blockchain security!
Table of Contents
ToggleWhat Is Hashing in Blockchain?

In blockchain, hashing is like turning information into a secret code. It takes a piece of data and uses a special method to crunch it down into a fixed-size jumble of letters and numbers, called a hash.
Even a tiny change in the data will totally change the hash. In blockchain, every block contains the hash of the previous block. This makes it super hard for anyone to mess with the information in a block without getting caught.
It’s like creating a chain of secret codes, where each code depends on the one before it, making the whole thing really secure.
Plus, these secret codes are made to be super tough to crack, adding an extra layer of protection to the blockchain.
There are different kinds of hash functions, like SHA-256 or SHA-3, but they all do the same job: keeping your blockchain secure by making sure nobody messes with the data.
How Hash Functions Operate in Blockchain

In blockchain, hash functions are like secret codes that keep everything safe.
When we hash data in blockchain, we’re turning it into a unique code using a special math formula. This code acts like a digital fingerprint for the original data.
Hash functions also help connect blocks together in a chain. Each block contains a code that’s based on the one before it, making it super hard to change past transactions without changing everything after.
Merkle trees help make sure everything stays honest by organizing transactions in a special way. They group transactions together and create a code for each group.
These codes are then linked together to make one big code that represents all the transactions. This helps keep the blockchain secure and trustworthy.
Securing Blockchain with Hash Functions
Securing Blockchain with Hash Functions is integral to maintaining the integrity and security of blockchain technology. Hash functions play a pivotal role in ensuring the immutability of the ledger, effectively preventing data tampering.
Each block in a blockchain contains a cryptographic hash of the previous block, creating a chain of blocks where any alteration to a previous block would invalidate all subsequent blocks, making it nearly impossible to tamper with historical data without detection.
Furthermore, hash functions are utilized in verifying transactions through two key processes: validating blocks and ensuring consensus.
Validating blocks involves hashing transactions and other block data to generate a unique identifier for each block, which is crucial for confirming the validity of transactions and maintaining the integrity of the blockchain.
Ensuring consensus among participants in the blockchain network relies on hash functions to reach agreement on the validity of transactions and the order in which they are added to the blockchain, thereby establishing a trustless and decentralized system.
The Connection Between Hashing and Proof of Work
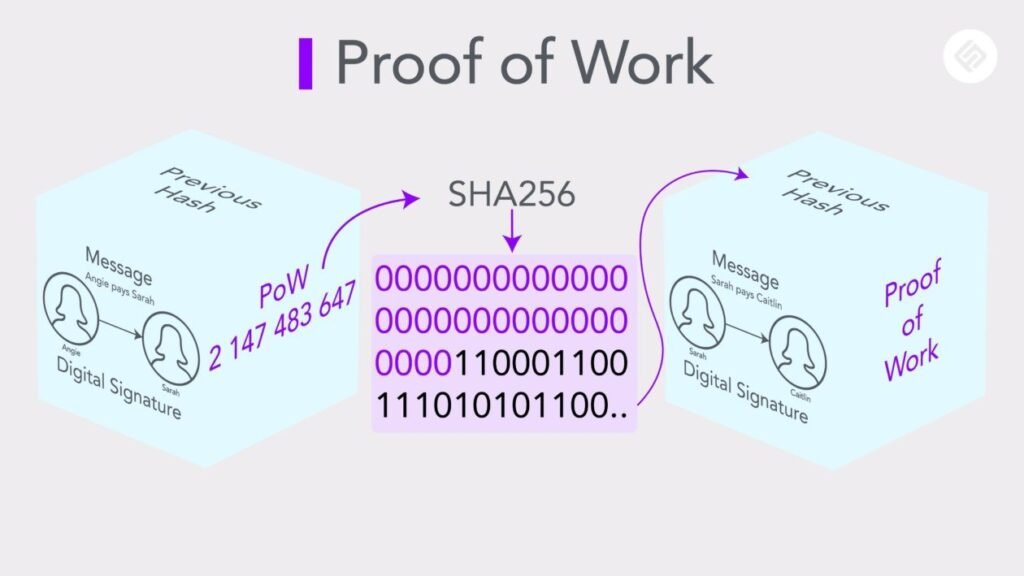
The connection between hashing and proof of work is fundamental to understanding how blockchain technology achieves security and consensus.
In the context of blockchain, mining involves solving complex mathematical puzzles through hashing algorithms. These algorithms take input data of any size and produce a fixed-size string of characters, known as a hash.
Miners compete to find a hash value that meets a certain criteria set by the network, which is known as the target or the mining difficulty. This process requires substantial computational power and energy expenditure.
The proof of work mechanism ensures miners invest significant resources to validate transactions and secure the network.
As more miners join the network, the difficulty of finding the correct hash increases, ensuring a consistent block generation rate and maintaining the blockchain’s integrity.
Adjusting mining difficulty dynamically ensures that blocks are generated at a predictable rate, balancing the network’s security and efficiency.
Therefore, the interplay between hashing and proof of work lies at the heart of blockchain security, providing a robust mechanism for consensus and trustless validation of transactions.
Cryptographic Hash Functions vs. Non-Cryptographic Hash Functions
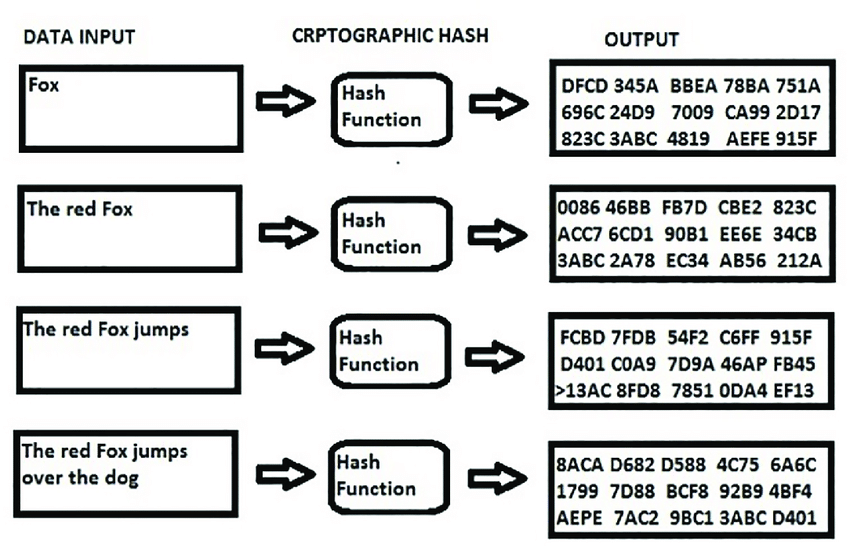
Cryptographic hash functions are pivotal in securing blockchain technology due to their unique characteristics.
These functions are designed to fulfill specific criteria to ensure robust security:
- Cryptographic hash functions possess the property of determinism, meaning that they consistently produce the same output for a given input, enabling verification processes within the blockchain.
- They exhibit the property of collision resistance, making it computationally infeasible to find two different inputs that produce the same hash value, which is crucial for maintaining the integrity of blockchain data.
- Cryptographic hash functions are irreversible, meaning it’s practically impossible to reverse-engineer the original input from its hash value, enhancing the immutability of blockchain records.
In blockchain security, cryptographic hash functions are extensively employed for various applications such as hashing transactions, creating digital signatures, and securing block headers.
However, non-cryptographic hash functions lack the stringent security properties required for blockchain applications, posing risks such as susceptibility to collision attacks and the potential for malicious tampering, making them unsuitable for ensuring the integrity and immutability of blockchain data.
Therefore, using cryptographic hash functions is paramount in maintaining the security and trustworthiness of blockchain technology.
Hashing Algorithms in Blockchain
In blockchain technology, hashing algorithms play a fundamental role in securing the data’s integrity.
Commonly used hashing algorithms include SHA-256, SHA-3, and RIPEMD-160. SHA-256 (Secure Hash Algorithm 256-bit) is widely utilized in significant blockchain networks like Bitcoin and Ethereum for its cryptographic strength and collision resistance, making it highly secure against unauthorized alterations.
However, its computational intensity can pose a challenge in specific applications, impacting performance. SHA-3, on the other hand, offers similar security features but with optimized performance, making it a preferred choice for some blockchain implementations.
RIPEMD-160 (RACE Integrity Primitives Evaluation Message Digest 160-bit) is often used with SHA-256 for specific purposes, such as address generation in cryptocurrencies.
While RIPEMD-160 is efficient and provides a shorter output size, its security level is comparatively lower than SHA-256 and SHA-3, which may pose risks in certain contexts.
Overall, each hashing algorithm has its strengths and weaknesses, and their selection depends on factors such as security requirements, performance considerations, and compatibility with existing protocols within the blockchain ecosystem.
Addressing Potential Vulnerabilities
Addressing potential vulnerabilities in blockchain technology is crucial for maintaining its security and integrity.
To mitigate the risk of a 51% attack, where a single entity gains majority control of the network’s mining power, blockchain protocols often employ consensus mechanisms such as Proof of Work (PoW) or Proof of Stake (PoS) to distribute mining power more evenly among participants.
This decentralization makes it exceedingly difficult for any entity to manipulate the network. Additionally, blockchain technology prevents double-spending by recording each transaction tamper-resistantly across multiple nodes, ensuring that it cannot be altered or duplicated once a transaction is confirmed.
Moreover, to resist Sybil attacks, where an attacker creates multiple fake identities to gain disproportionate influence, blockchain networks require participants to prove their identity or stake tokens, making it costly and impractical for attackers to develop numerous counterfeit identities and manipulate the system.
These measures collectively strengthen the security of blockchain technology and enhance its resilience against potential vulnerabilities.
Evolving Landscape of Hash Functions in Blockchain
The evolving landscape of hash functions in blockchain technology has witnessed significant advancements in recent years.
A. Innovations in hash functions have played a crucial role in enhancing the security and efficiency of blockchain networks. Various cryptographic techniques such as SHA-256 and SHA-3 have been widely adopted, providing robust mechanisms for hashing data within blocks.
Moreover, emerging algorithms like BLAKE2 and Keccak offer improved performance and resistance against certain types of attacks, further fortifying blockchain systems.
B. With the looming threat of quantum computing, which poses a significant risk to traditional cryptographic methods, hash functions have been scrutinized for their vulnerability.
However, ongoing research endeavors have led to the development of quantum-resistant hash functions like SHA-3 and BLAKE2b, ensuring the resilience of blockchain networks against potential quantum threats.
C. Scalability remains a persistent challenge for blockchain platforms, necessitating innovative solutions to enhance throughput and accommodate growing transaction volumes.
Hash functions have been integral to scalability solutions such as sharding, where the blockchain is divided into smaller, manageable segments, each with its own set of validators and hash functions to maintain security and consensus.
Additionally, advancements like DAG (Directed Acyclic Graph) structures, as seen in projects like IOTA, employ hash functions to enable asynchronous and parallel transaction processing, addressing scalability concerns in a decentralized manner.
In essence, the continuous evolution of hash functions plays a pivotal role in shaping the security, resilience, and scalability of blockchain technology amidst evolving threats and challenges.
Comparing Energy Consumption: Bitcoin vs. Ethereum
When comparing the energy consumption of Bitcoin and Ethereum, it’s evident that Bitcoin’s mining process is significantly more energy-intensive than Ethereum’s current mechanism.
Bitcoin relies on a proof-of-work (PoW) consensus algorithm, where miners compete to solve complex mathematical puzzles to validate transactions and create new blocks.
This process demands substantial computational power, resulting in a high energy consumption rate.
On the other hand, Ethereum has been transitioning from proof of work to proof of stake (PoS) with its Ethereum 2.0 upgrade. Proof of stake replaces miners with validators who are chosen to create new blocks based on the amount of cryptocurrency they hold and are willing to “stake” as collateral.
This shift aims to drastically reduce Ethereum’s energy consumption, making it more environmentally friendly than Bitcoin’s energy-intensive mining process.
Future Prospects and Research Directions
Future Prospects and Research Directions in the realm of blockchain security are promising, with several key areas warranting attention:
- Advancements in hash function technology hold significant potential for enhancing blockchain security. Researchers are continuously exploring novel cryptographic primitives and hash functions to bolster resistance against potential attacks. This includes developments in post-quantum cryptography to mitigate the threat posed by quantum computing.
- Addressing emerging threats remains crucial. As blockchain technology evolves, new vulnerabilities and attack vectors may arise, necessitating proactive measures to identify and mitigate risks effectively. This involves ongoing research into potential vulnerabilities such as consensus algorithm flaws, smart contract vulnerabilities, and network attacks.
- Interdisciplinary collaborations are essential for fostering a holistic approach to blockchain security.
Collaboration between cryptographers, computer scientists, economists, legal experts, and industry stakeholders can facilitate the development of comprehensive security frameworks and regulatory measures.
By integrating insights from diverse fields, researchers can better understand blockchain technology’s multifaceted challenges and develop robust solutions to safeguard its integrity and resilience.
Conclusion
In short, hash functions are super important for keeping blockchain safe. They make sure that no one can mess with transactions without getting caught.
As blockchain gets better, hash functions will stay really important for keeping everything secure.
In the future, we might see even better ways to use hash functions that make blockchain faster and safer.
So, understanding how hash functions work helps us trust blockchain more and use it in lots of different ways.
Hopefully, I have fulfilled your search intent in this article. If you really liked the content then share with others and also subscribe to our email newsletter to keep receiving the updates in cryptocurrency niche.
Frequently Asked Questions
What is hashing in blockchain with example?
Hashing in blockchain is the process of converting input data into a fixed-size string of characters using a cryptographic hash function. This process ensures data integrity and security within the blockchain network. For example, in Bitcoin, each block contains a hash of the previous block's header, creating a chain of blocks linked together through cryptographic hashes.
What is the difference between encryption and hashing?
Encryption is the process of converting data into a ciphertext using an encryption algorithm and a key. It is reversible, meaning the original data can be recovered using the decryption key.
Hashing, on the other hand, is the process of converting data into a fixed-size string of characters using a cryptographic hash function. It is irreversible, meaning the original data cannot be recovered from the hash.
In summary, encryption is reversible and used for protecting data confidentiality, while hashing is irreversible and used for data integrity and security verification.
How does Proof of Work relate to hashing in blockchain?
Proof of Work (PoW) in blockchain relies heavily on hashing. PoW involves miners competing to solve complex mathematical puzzles by repeatedly hashing potential block header values until finding one that meets certain criteria (such as having a specific number of leading zeros). This process requires significant computational power and energy expenditure.
Hashing plays a crucial role in PoW by providing the mechanism for miners to demonstrate their work. The hashed output of each block header serves as a unique identifier, and miners must find a nonce value that, when combined with the block data, produces a hash that meets the difficulty target set by the network.
How blockchain technology is secure?
Blockchain technology is secure due to its decentralized and immutable nature. Security in blockchain is achieved through cryptographic techniques such as hashing, digital signatures, and consensus mechanisms like Proof of Work or Proof of Stake.
- Decentralization: Instead of relying on a single central authority, blockchain operates on a distributed network of nodes, each storing a copy of the ledger. This decentralization makes it resistant to single points of failure or attacks.
- Immutable Ledger: Once data is recorded on the blockchain, it becomes virtually impossible to alter or delete it due to cryptographic hashing. Each block contains a hash of the previous block, creating a chain of blocks that are inherently resistant to tampering.
- Cryptography: Blockchain uses cryptographic algorithms to secure transactions and ensure data integrity. Digital signatures authenticate the identity of participants, while hashing ensures the integrity of data stored on the blockchain.
- Consensus Mechanisms: Consensus algorithms like Proof of Work or Proof of Stake ensure agreement among network participants on the validity of transactions. This prevents double-spending and ensures the security and integrity of the blockchain.
Can hash functions be reversed?
No, hash functions cannot be reversed. Hash functions are designed to be one-way functions, meaning it is computationally infeasible to reverse the process and obtain the original input data from the hash output.
What happens if a hash collision occurs in the blockchain?
If a hash collision occurs in the blockchain, two pieces of data produce the same hash value. This event compromises the integrity of the blockchain, as it violates the unique property of hashes. It can lead to potential security vulnerabilities and undermine the reliability of the blockchain's data. Promptly resolving hash collisions is crucial to maintaining the integrity and security of the blockchain network.







[…] Bitcoin mining, the target is represented by a hash—a 64-digit hexadecimal number. Miners use their computational power to find a hash that meets […]